Second Initial Idea
Network Forensics (INITIAL IDEA 2)
The requirement for network forensics is rising, as more and more organisations want to know how their services are being accessed and used (Infosecurity,2010).
Network forensics is a branch of digital forensics relating to uncovering, collecting, examining and interpreting electronic data evidence found in networks and various other crime-related digital devices in a way it is acceptable in a court of law.
Rather than relying on data from operating systems and disks, network forensic investigators focus on the network itself and collect data of an attack in progress or after a security breach. This data could then be observed and pieced together to form a coherent picture which may include information from numerous sources such as application logs and firewalls (Messier, 2017).
An example of a technique used in evidence handling would be cryptographic hashing, which is a computational, mathematical process that generates a unique, fixed, numeric value for the hashed evidence (Messier, 2017).
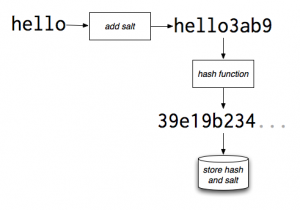
Hashing is easy to perform but very difficult to reverse, which is the main difference between it and encryption (Encrypted data could be reversed by decrypting it using a specific key). The most commonly used hashing functions included MD5, SHA1 AND SHA-256. Reversing a hash is difficult, not impossible, however, there are certain techniques that can be used to make it harder to be cracked. One method includes 'salting' which is the process of adding random key/string to the plaintext. An example of this would be a string of 'hello' which would then become 'hello3ab9' post-salting. This string value will then be giving a new value once hashed, different than the previous one.
Moving on, a specific software that will be used in this essay would include Wireshark, which is a free and open-source packet analyser.
Wireshark is mainly used for:
- troubleshooting networks.
-Analysing a network.
- Used for software aad communication protocol development.
-Used in the field of education.
Reference(s):
Infosecurity (2010) Network forensics helps bolsters confidence in cloud computing security. Available: http://www.infosecurityus.com/view/13252/network-forensics-helps-bolstersconfidence-in-cloudcomputing-security/. [31 Mar 2016]
Messier, R., (2017). Network Forensics. [Place of publication not identified]: Wiley & Sons.
Thadani, R., (n.d). Password-Hash-Salt. [image] Available at: <https://blogs.quickheal.com/wp-content/uploads/2012/06/password-hash-salt-e1339412863205.png> [Accessed 8 November 2020].
Network forensics is a branch of digital forensics relating to uncovering, collecting, examining and interpreting electronic data evidence found in networks and various other crime-related digital devices in a way it is acceptable in a court of law.
Rather than relying on data from operating systems and disks, network forensic investigators focus on the network itself and collect data of an attack in progress or after a security breach. This data could then be observed and pieced together to form a coherent picture which may include information from numerous sources such as application logs and firewalls (Messier, 2017).
An example of a technique used in evidence handling would be cryptographic hashing, which is a computational, mathematical process that generates a unique, fixed, numeric value for the hashed evidence (Messier, 2017).
Hashing is easy to perform but very difficult to reverse, which is the main difference between it and encryption (Encrypted data could be reversed by decrypting it using a specific key). The most commonly used hashing functions included MD5, SHA1 AND SHA-256. Reversing a hash is difficult, not impossible, however, there are certain techniques that can be used to make it harder to be cracked. One method includes 'salting' which is the process of adding random key/string to the plaintext. An example of this would be a string of 'hello' which would then become 'hello3ab9' post-salting. This string value will then be giving a new value once hashed, different than the previous one.
(Thadani, n.d.)
Moving on, a specific software that will be used in this essay would include Wireshark, which is a free and open-source packet analyser.
Wireshark is mainly used for:
- troubleshooting networks.
-Analysing a network.
- Used for software aad communication protocol development.
-Used in the field of education.
Reference(s):
Infosecurity (2010) Network forensics helps bolsters confidence in cloud computing security. Available: http://www.infosecurityus.com/view/13252/network-forensics-helps-bolstersconfidence-in-cloudcomputing-security/. [31 Mar 2016]
Messier, R., (2017). Network Forensics. [Place of publication not identified]: Wiley & Sons.
Thadani, R., (n.d). Password-Hash-Salt. [image] Available at: <https://blogs.quickheal.com/wp-content/uploads/2012/06/password-hash-salt-e1339412863205.png> [Accessed 8 November 2020].

Second idea is about network forensics, but title says otherwise.
ReplyDeleteVery good, gives us a brief overview about network forensics but we need to learn more about this such as the techniques used, the software used, the outcome of a network forensic investigation.